Cisco ASA with IPSec/VPN for Apple iOS
Step by step guide
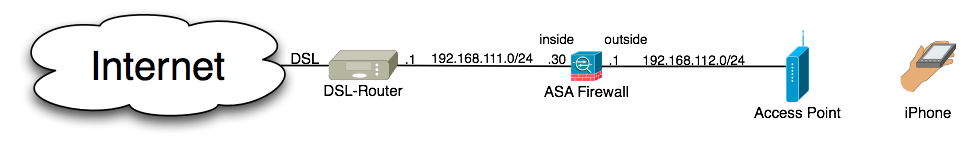
We start with a clean factory default config
This will erase you current config!!!
ciscoasa> enable
ciscoasa# conf t
ciscoasa(config)# configure factory-default
ciscoasa(config)# write men
ciscoasa(config)# reload
Now you should have a default config similar to
ASA5520ShowRun
Very simple working config without any VPN
interface GigabitEthernet0/0
nameif inside
security-level 100
ip address 192.168.111.30 255.255.255.0
!
interface GigabitEthernet0/1
nameif outside
security-level 0
ip address 192.168.112.1 255.255.255.0
!
interface Management0/0
shutdown
no ip address
!
access-list inside_acl extended permit icmp any any
access-list inside_acl extended permit ip any any
access-list outside_acl extended permit icmp any any
access-list outside_acl extended permit ip any any
access-group inside_acl in interface inside
access-group outside_acl in interface outside
route inside 0.0.0.0 0.0.0.0 192.168.111.1 1
!
no http 192.168.1.0 255.255.255.0 management
http 192.168.111.0 255.255.255.0 inside
!
no dhcpd address 192.168.1.2-192.168.1.254 management
no dhcpd enable management
dhcpd address 192.168.112.10-192.168.112.40 outside
dhcpd dns 192.168.111.1
dhcpd enable outside
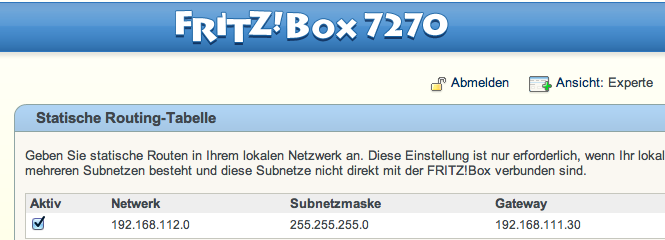
Additionally i have to add a static route from my dslbox to the net behind my firewall.
Here an example from my FritzBox:

Now you should be able to connect with your iPhone and surf in the internet without any VPN and without any security. This is just a test that the principle setup works.
Connect to VPN Wizard in the ASDM-GUI
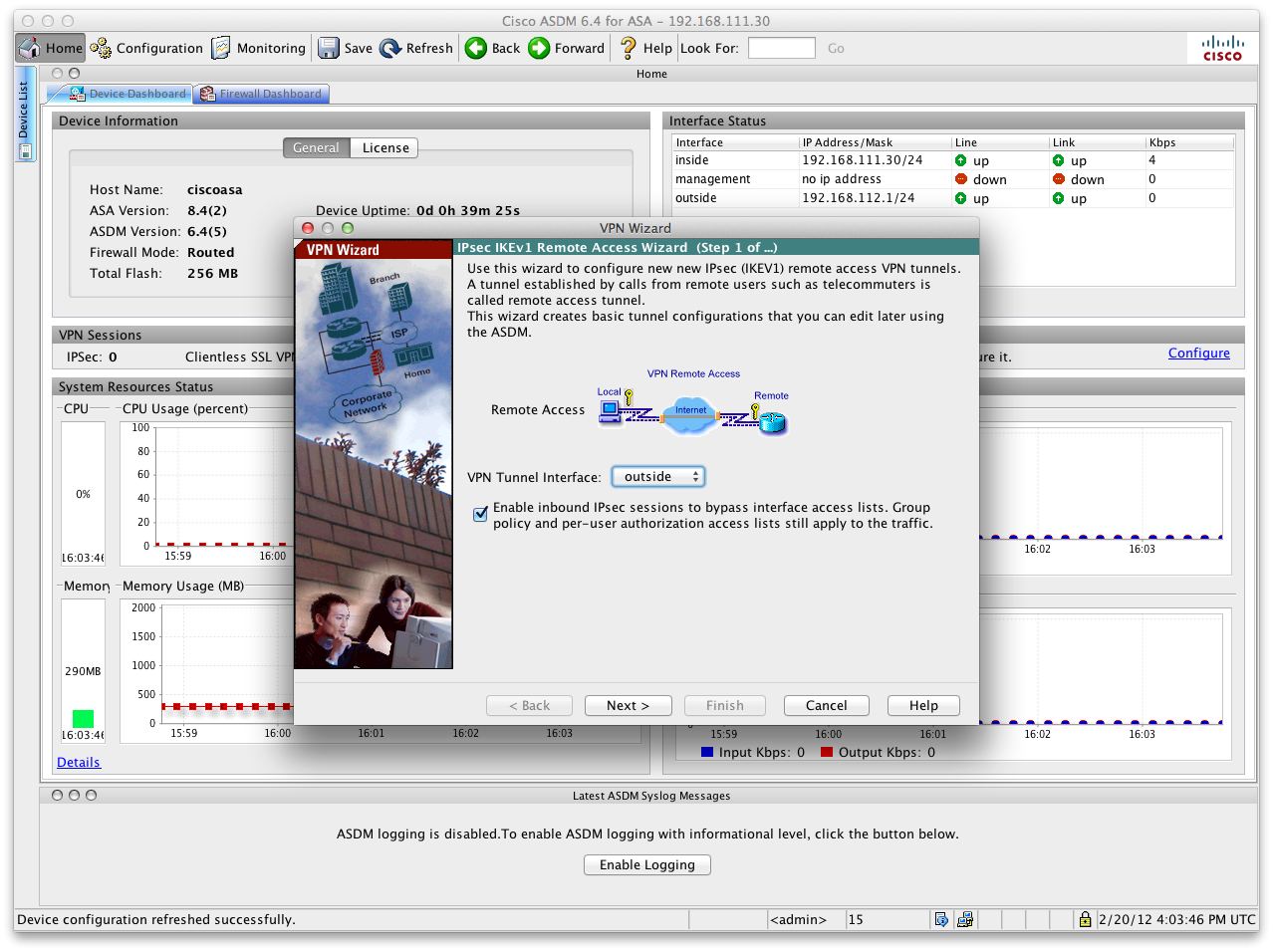
together with the
setup guide from Apple
Or use the CLI commands that the wizard produces
object network NETWORK_OBJ_192.168.111.32_28
subnet 192.168.111.32 255.255.255.240
!
ip local pool VPNPOOL 192.168.111.32-192.168.111.40 mask 255.255.255.0
!
nat (inside,outside) source static any any destination static NETWORK_OBJ_192.168.111.32_28 NETWORK_OBJ_192.168.111.32_28 no-proxy-arp route-lookup
!
crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set pfs
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map outside_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map outside_map interface outside
crypto ikev1 enable outside
crypto ikev1 policy 10
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
!
group-policy IOSVPN internal
group-policy IOSVPN attributes
dns-server value 192.168.111.1
vpn-tunnel-protocol ikev1
username joe password GQe4s1ZATOf6A28O encrypted privilege 0
username joe attributes
vpn-group-policy IOSVPN
tunnel-group IOSVPN type remote-access
tunnel-group IOSVPN general-attributes
address-pool VPNPOOL
default-group-policy IOSVPN
tunnel-group IOSVPN ipsec-attributes
ikev1 pre-shared-key *****
I use the password
1234567890 for user joe and pre-shared-key in this example.
Go to
Settings > General > Network > VPN > Add VPN Configuration
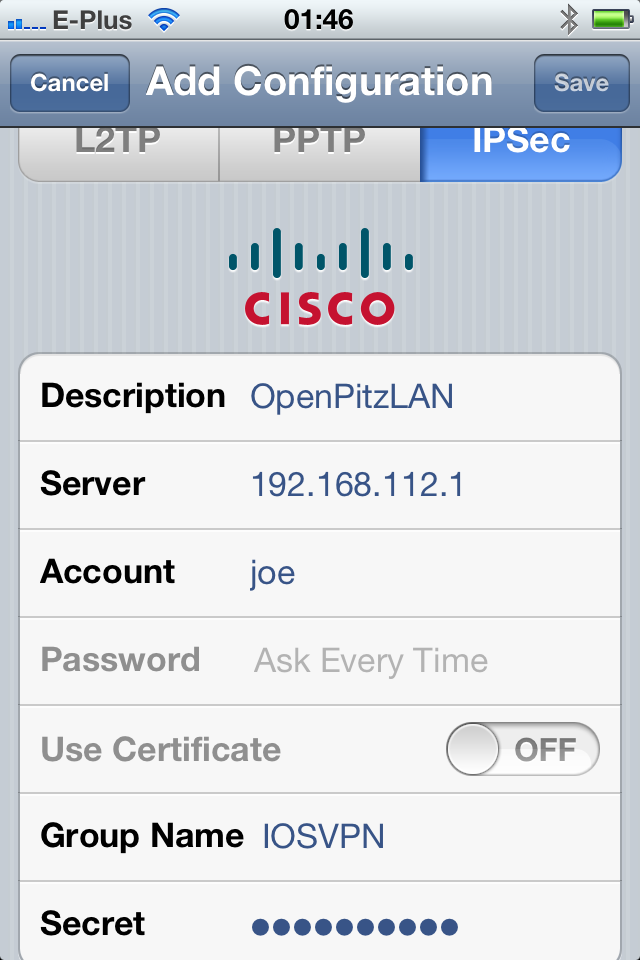
Add a ACL so that the setup is secure and you can connect only through the VPN-tunnel
access-list outside_acl line 1 extended deny ip any any
Now you can safely connect through VPN
PCF File
The VPN server can be found after Host= in the pcf file. Group Name is after
GroupName=, Group Password is after enc_GroupPwd= or
GroupPwd=. Asterisks added below for emphasis.
[main]
Description=OpenPitzLAN
Host=192.168.111.1
AuthType=1
GroupName=IOSVPN
GroupPwd=1234567890
enc_GroupPwd=
EnableISPConnect=0
ISPConnectType=0
ISPConnect=
ISPCommand=
Username=joe
SaveUserPassword=1
UserPassword=1234567890
enc_UserPassword=
NTDomain=CorpDomain
EnableBackup=0
BackupServer=
EnableMSLogon=1
MSLogonType=1
EnableNat=1
CertStore=0
CertName=
CertPath=
CertSubjectName=
CertSerialHash=00000000000000000000000000000000
DHGroup=2
ForceKeepAlives=0
PeerTimeout=90
ASAFullWorkingVpnIosConfig
Decode Cisco Shared Secret Password 'encryption'


 together with the setup guide from Apple
together with the setup guide from Apple

